As you likely already know if you’re reading this, GCDS (formerly known as Google Apps Directory Sync aka GADS) is a tool for synchronizing an Active Directory or LDAP server to a Suite domain. This article is a description of my first foray into working with this program.
1. Preparation. The environment is a VM running a fresh install of Windows Server 2012 R2 64-bit, with vanilla setups of DNS and AD. This server is authoritative for a made-up domain called “whoopis.in” and the server’s name is “pustule” (sorry.) I am using the Windows Administrator account (knowing that IRL I’d use a different domain-admin-capable account.) My GSuite domain is whoopis.com.
This is what my AD structure looks like:
And this is what my GSuite structure looks like:
So, I’ve got an OU in GSuite called “Restricted" that I do NOT have in my AD, and I’ve got some users at the top level of the GSuite OU who don’t exist in AD, but otherwise the hierarchy is the same.
2. LDAP Configuration. Because I am an LDAP n00b to begin with, just getting the thing to talk to AD at all was a small struggle. It prompted for the one-time “allow this app to make API calls against your Google domain” which I didn’t bother to screenshot, but then I did some trial and error to get it to connect to AD. These are the settings that worked:
That slightly-truncated Authorized User line is, in its entirety:
cn=Administrator,cn=Users,dc=whoopis,dc=in
3. LDAP Mapping. So then, on the Org Units page -> LDAP Org Unit tab, I click the Add Mapping button:
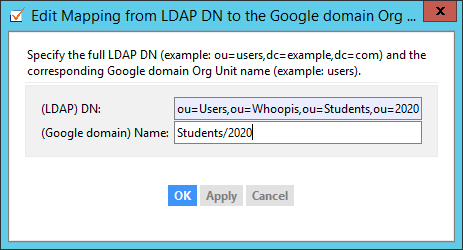
Again, slightly truncated, but you can see it in its entirety after you hit OK:
4. User attributes. This part is a bit of an aside, but thanks to Nick Sintros’s beautiful notes/screenshots, this is one easy way to map multiple email aliases by using other fields in AD:
Then, add those on the User Atrributes tab of the User Accounts page:
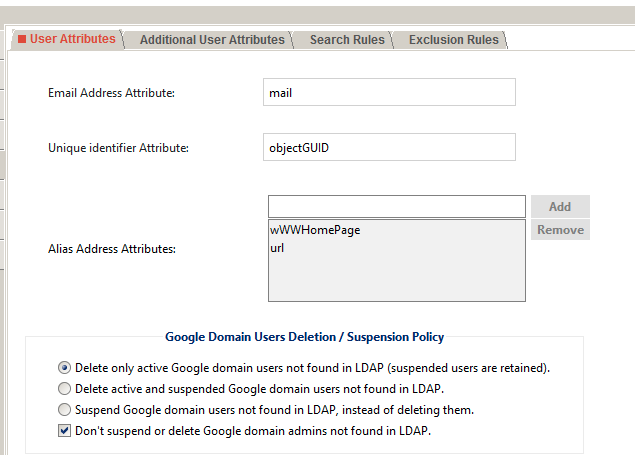
(I am not sure about the cAsE in that first one — I copied what was in Nick’s screenshot EXACTLY, and it worked, so I left it alone.)
I am not entirely certain about the Unique identifier Attribute — it was either prefilled, or I read somewhere that that’s what other people use. My understanding is that you should NOT use name or email, because those things can change (marriage etc.)
Note carefully the bottom section, “Google Domain Users Deletion/Suspension Policy.” I wish it had an option for “Add if missing, skip over if not” — but, it doesn’t. It wants to be a destructive sync. So watch your ass here.
5. Search rules. For me, this part should be called “here be dragons.” I copypasted the LDAP rule syntax from Google’s examples documentation.
Basically, I mashed that “Test LDAP Query” button until it reported success, but I don’t know if these are the settings that I WANT — more on that soon.
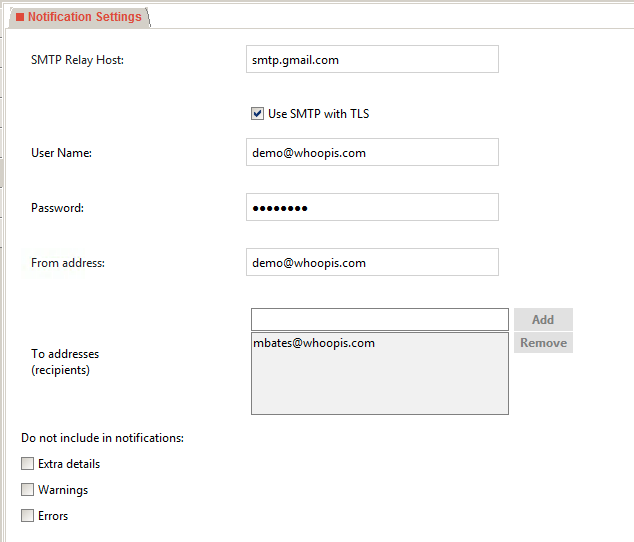
6. Notification options. I would’ve liked to just skip this section altogether initially, but the tool REQUIRES it to be set up, and THAT led me down a pretty stupid rabbit hole of FIXME another howto on enabling insecure email. But finally this worked:
7. Simulate. Thank the Google Gods for this button:
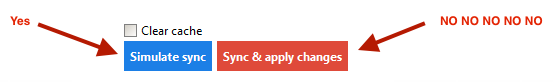
It chunks along for a bit and then displays something like this:
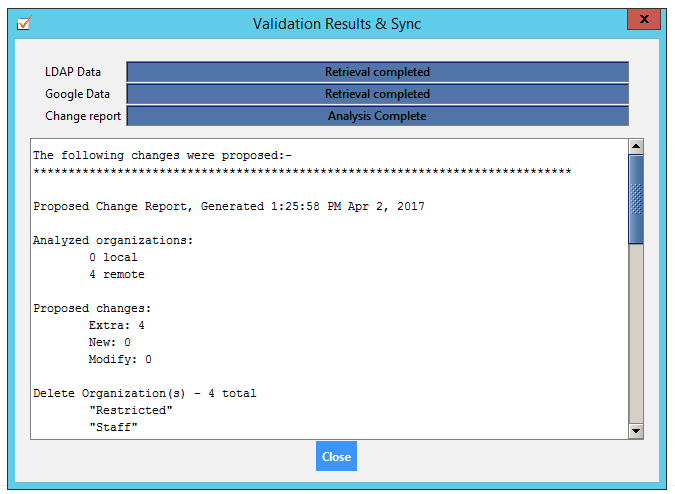
Here’s the entire text of that:
The following changes were proposed:- ***************************************************************************** Proposed Change Report, Generated 1:25:58 PM Apr 2, 2017 Analyzed organizations: 0 local 4 remote Proposed changes: Extra: 4 New: 0 Modify: 0 Delete Organization(s) - 4 total "Restricted" "Staff" "Students" "Students/2020" Analyzed users: 1 local 5 remote Proposed changes: Delete: 0 Modify: 3 Create: 1 Modify (all proposed changes) - 3 total users affected Modify user 1: "demo@whoopis.com" Suspend user Modify user 2: "pbates@whoopis.com" Suspend user Modify user 3: "vberk@whoopis.com" Suspend user Create - 1 total New user 1: "joe.freshman@whoopis.com" Org "/" Non-address primary key "Nl85q0i-n0GWfv5N4UAQIw" SHA1 password 2 aliases "joe.freshman@dresden.us" "joe.freshman@marioncross.org" Click here to view logs
So, as you can see, this isn’t exactly what I had in mind, haha. The next phase is for me to learn more about search rules and exclusions etc. and do some more experimentation. To be continued!