Firewalling
on OS X - Part
2
Brickhouse’s
Add Filter dialog box. Has a lot of presets, or you can create
custom ones.
|
The
Advanced Options button lets you specify flags and toggle
logging for that rule.
An odd caveat: I had to make an allow rule for SSH inbound
from my IP to my IP in order to tunnel SSH from Classic (even
though they have the same IP!) If you
encounter this sort of strangeness between Classic and X, check your firewall
settings. This may not be necessary anymore in 10.2.
Another note: In 10.2, if you want to be able to browse local Windows domains
and shares (as opposed to just connecting to them if you know their names), then
you’ll need to add an allow rule for UDP traffic with destination port
137 destined for your Mac. |
|
Useful
Tools - Network Utility
• ping
•
traceroute
•
whois
•
nslookup
•
netstat
•
finger
•
a port scanner (careful with that one.) |
 |
|
| In
most, if not all cases, these tools will work better and/or
have more options if you use them from the CLI. Especially
netstat. (netstat -an | less) Know the Terminal. Love the
Terminal. |
|
Useful
Tools - Keychain
|
| Keychain
can store your passwords for frequently-accessed things,
and prompt you for your Keychain uber-password to unlock
the other passwords. Many apps are Keychain-aware (such as
MacSFTP -- keeps you from having to re-enter your password
for every SCP operation you perform). It goes without saying
that your Keychain password ought to be very secure. |
|
Useful
Tools - Process Viewer
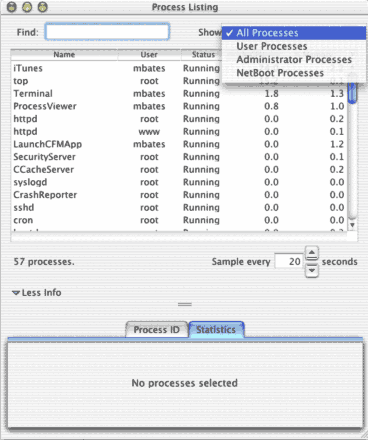
| GUI
for the Unix top command. Shows which apps are running
on your Mac. |
 |
|
| From
here, you can select a process and the Process ID and Statistics
tabs will display information about it. You can also go to
the Processes menu and select “Quit Process” to
kill it. |
|
<<Back | Index | Next >>
|