Fetch
security options
From
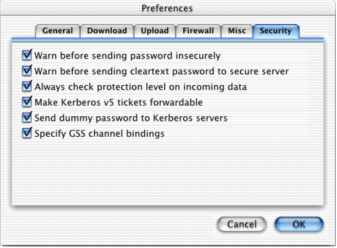
Fetch’s Customize menu, select Preferences and
click the Security tab.
|
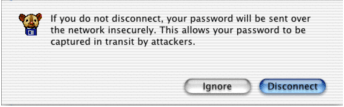
You’ll
see this when you connect:
|
|
| Since
the Kerberos thing is difficult or impossible to use, we can
at least take advantage of the basic security features. Under
Fetch’s Security preferences, checking the top two boxes
will not make your connection secure, but at least it will
remind you when you’re about to expose your password. |
|
E-Mail
Normal POP/POP3 mail is unencrypted
But, most
major email clients support SSL
•
Mail server(s) must support it too
Eudora
and Outlook both have SSL option
•
Protects your password
and content
•
Only for the path between your Mac and
your ISP.
Next hop mail server may not.
Always assume that
your mail message is not going to be secure for its entire
journey to the recipient. |
| Normal
POP/POP3 mail is unencrypted, but most major email clients
support some level of extra security (but again, the mail server(s)
must support those features as well). Eudora and Outlook both
have an option for email over SSL, which if supported on your
service provider’s server, protects your password and
the email content -- but only for the path between your Mac
and your ISP. The next mail server down the line may not have
SSL, so you should always assume that your mail message is
not going to be secure for its entire journey to the recipient.
Eudora also supports APOP (Authenticated Post Office Protocol)
which encrypts your password (though not as securely as SSL).
There is also S/MIME, in which both the sender and recipient
use certificates to sign or encrypt email (sort of PGP-esque). |
|
PGP
The
encryption lecture covers the details of PGP. At least one PGP
client for the Mac
•
PGP.com (formerly Network Associates,
Inc.) has “PGPFreeware” (v. 7.0 at the time of this
writing) for OS 9 and “PGP 8.0 LIVE” for OS X.
•
Free
for academic use
•
Compatible with other flavors of PGP
(such as GPG).
For OS X, there is also GPG (GNU Privacy Guard)
-- more on that later. |
NPGP,
or Pretty Good Privacy, will be/has been discussed in depth
in another class, so we won’t go into detail here. There
is at least one PGP client for the Mac, which plugs in nicely
to Eudora and probably Outlook, and which also provides an
easy way to interact with non-standard email clients (like
BlitzMail).
The client I use is made by PGP.com (formerly Network Associates,
Inc.) and is
called simply “PGP” (v. 7.0 at the time of this writing). It’s
free for academic use, and it’s compatible with other flavors of PGP (such
as GPG).
You can get GPG for OS X, and at this time the GUI is still kinda clunky, but
it works if you follow the directions carefully when you set it up. |
|
Attachments
(“Enclosures”)
Most
common way of getting a virus or other malware is via email attachments
Lots of clever tactics to lure you into opening something that
looks legit…beware!
As a Dartmouth Mac user, you have a
rare advantage -- BlitzMail. It…
•
doesn’t
download attachments automatically
•
doesn’t interpret
HTML mail (spammers send HTML mail with bad Javascripts etc.)
•
isn’t
Outlook ;) |
Probably
the most common way of getting an unwanted program (such as
a virus) is by receiving
an attachment in email. In the last couple years, there have
been a huge number of worms which infect Windows machines via
the Outlook email program. This is not directly dangerous to
Mac users, but it serves to illustrate a point. The recent “Klez” virus/worm
used several tactics to increase the likelihood that a recipient
of the virus would open the attachment; it would pull email addresses
out of the user’s address book or web cache, and create
Subject lines from bits of documents or cached webpages on the
victim’s computer, then generate more emails from those.
The result was that other victims would receive email from people
they knew, with message content that looked familiar. What a
lure!
The point here is that, while Klez posed no threat to Mac users
(even Mac Outlook users), the methods used by Klez demonstrate
that viruses can be pretty clever.
Be certain, before you open an attachment, that the sender really
is the sender,
and that it’s someone you trust. Even then, you should scan the file with
your antivirus software before you open it. Norton and others can be easily configured
to “quarantine” and check new files before you use them. |
|
More
on email at Dartmouth
• BlitzMail
hides password (challenge-response)
•
Comp Svcs is currently
testing software to automatically filter/alert on virus-ridden
email before it even gets to you
•
Also, there are plans
to make the servers fully IMAP-compliant (beta testing now)
•
But,
the session is still clear text. Your messages can be read. |
| Dartmouth’s
BlitzMail system provides a simple, easy-to-use, yet powerful
interface for electronic mail. Its simplicity and uniqueness
also add to its security; BlitzMail is immune to all the Outlook
email viruses, since it does not arbitrarily download or execute
code of any sort. It also does not have HTML mail capability,
which thwarts a great deal of spam email containing JavaScripts
and other “spyware” elements. Macintosh BlitzMail
versions since 2.0.5 will even detect a keystroke logger running
on the user’s machine, and will not only alert the user
to this fact, but will also scramble the keystrokes as they
are written to the keystroke logger’s result file, so
the malicious user cannot see what was typed. |
|
BlitzMail’s
brethren
Other
secure ways to use Blitz:
•
WebBlitz (Basement)
•
NetBlitz
(my favorite, if the regular client is unavailable)
•
TextBlitz
via SSH (old and primitive, but works in a pinch) |
In
addition to the real BlitzMail client, there are other secure
ways to use Blitz.
WebBlitz -- Uses
SSL to protect your session.
NetBlitz -- a streamlined web-based client.
Has
multiple security options -- you can SSL-encrypt just your login,
or your whole session, depending on how much speed vs. security
you care about.
TextBlitz -- very bare-bones Blitz access. SSH to textblitz.dartmouth.edu as
user “blitz” with no password. You’ll be prompted for your
BlitzMail login info. You can only read what’s in your inbox. This is very
old. |
|
Viruses!
Not
really a big deal for Macs (so far).
•
Again, small user
base and the uniqueness of MacOS = small target
•
Most
recent big one: Word macro virus (which affected Word documents
on all platforms)
•
Also, a worm or two |
Not
a big deal for Macs. There just aren’t very many viruses
out there. Again, the small user base and the uniqueness of
MacOS make it a small, unattractive target for most of the
virus-writing twits in the world.
Probably the most dramatic one in recent history was the Word
macro virus (which affected Word documents on all platforms,
not just the Mac). It wasn’t
super-destructive, but it did manage to irritate just about everybody at Dartmouth
for a few months.
Macro scripting language is supposed to be used for creating in-document shortcuts
for repetitive functions. The macro scripting language developed by MS apparently
can do much more, because a couple years back there was a huge epidemic of macro
viruses in Word documents on Windows and Mac (mostly affecting Word version 6).
These viruses did a variety of cute things, like alter your “Normal” Word
template such that every Word document you opened or created would be infected,
and/or embed a chunk of text in every Word document you ever opened, that you
could NOT remove from the document (the text contained a message about a Scrabble
game), and one variant could even hide a menu in the program (!) which you had
to use in order to get rid of the virus! (I thought I had gone insane. The cleanup
instructions said “1. Go to the Tools menu” and there WAS NO TOOLS
MENU.) |
|
Countermeasures
3
or 4 other known Mac viruses
•
Some do have destructive
payloads
•
Rate of infection is very low Run Norton Antivirus
or equivalent
List and description of Mac viruses:
http://www.symantec.com/mac/security/macattack.html |
The
macro virus thing is pretty much over. Word98 and up have macro
support disabled by default and/or built-in macro virus detection.
Also, antivirus utilities such as Norton are able to detect
and clean or at least quarantine documents containing macro
viruses.
The other fairly-memorable and somewhat recent Mac malware
was a worm. It used
QuickTime’s “autoplay” feature (which starts playing audio
CDs as soon as they’re inserted) and some strains of the worm would destroy
files with .dat or .data name extensions, but mostly all it did was start up
Print Spooler and slow your system down. All you had to do to avoid infection
was turn off the autoplay feature in QuickTime.
There are 3 or 4 other known Mac viruses, some of which do have destructive payloads
(delete random files, interfere with loading of extensions, etc.) But the rate
of infection is very low. If you’re paranoid, which is a good thing, run
Norton Antivirus or another AV program. It’s a good idea to boot off the
CD and have it scan your system BEFORE you install it, since some viruses try
to disable AV programs. Hold down the C key to boot off a CD.
List and description of Mac viruses:
|
|
Firewalls
The
firewall lecture covers how they work. Mac ones:
•
Norton
Personal Firewall for Macintosh
•
OS X has built-in firewall
software
In general, firewall software should:
•
Have basic
and advanced user modes
•
Have good logging and notification
options
•
Support multiple rule sets
•
Be able to
export logs in standard formats
•
Support multihoming
•
Ideally,
support egress filtering |
The
firewall lecture in this class covers what firewalls do and how
they work. Norton Personal Firewall for Macintosh is a good choice.
(OS X has built-in firewall software, but we’ll get into
that later.)
A good firewall should be easy to use, have basic and advanced
user modes, and have good logging (and should be able to export
logs in standard formats, so
you can analyze the logs with another program). It ought to support multihoming
(I.e., separate rules for different network interfaces or locations, especially
for PowerBook users), and ideally, filtering of outbound traffic (e.g., prevent
your credit card number from being sent in a clear text format, or stop traffic
destined for known Trojan horse ports.) A decent fw program should also allow
you to have multiple sets of rules. You ought to be able to easily create a basic
ruleset with high-security rules (the default set, preferably). There should
be notification options (for example, Norton can pop up mini-windows telling
you about access attempts right as they happen).
Ideally, your fw should have the abilitiy to silently drop OR explicitly reject
traffic. And it should be stateful. But these last two features are pretty frequently
left out of “personal” firewalls. If you really want to have these
features, get a cheap old PC, install two cheap NICs, and put Linux with Netfilter
on it for a dedicated, powerful, stateful inspection firewall and put your Mac
behind it. :) But that’s kinda overkill.
|
|
<<Back | Index | Next >>
|